OpenVPN access server is a tool that allows for the rapid installation & configuration of a VPN server. It is commercial software however the ‘free’ license allows for 2 concurrent connections.
My server LAN IP is 192.168.1.1 and there is an intranet web server on 192.168.1.2 The OpenVPN daemon is configured to give clients 192.168.2. addresses. There is push 'route 192.168.1.0 255.255.255.0' line in the config which I expect to enable the VPN clients to access the entire 192.168.1.0 net, but they can only access 192.168.1.1 - the. OpenVPN Access Server is a full featured SSL VPN software solution that integrates OpenVPN server capabilities, enterprise management capabilities, simplified OpenVPN Connect UI, and OpenVPN Client software packages that accommodate Windows, MAC, and Linux, mobile OS (Android and iOS) environments. OpenVPN Access Server (10 Connected Devices) By: OpenVPN Inc Latest Version: 2.8.5. Transform your business with a secure and powerful Virtual Private Network (VPN) software from OpenVPN Inc. OpenVPN Access Server supports a wide range of configurations, making it one of the most flexible secure virtual networking solutions available.
In this guide I am going to show you how to configure the access server, generate certificates for your domain & automatically renew them every 3 months.
Requirements:
- A domain name pointing to your external IP, I will be using ‘example.com’.
- A computer running linux (Open VPN access server has not been built for ARM therefore it cannot be a raspberry pi), the internal server/computer will need a static IP to ensure there are no port forwarding issues.
All of the commands in this guide will need to be run as ‘root (sudo -s)’
For more information on other distributions the information can be found here: https://openvpn.net/vpn-software-packages/
Once installation is completed we need to create a password for the user ‘openvpn’ using the command:
We then need to login to the admin portal (https://your-server-ip:943/admin).
You will get an ‘not secure’ warning as the server is currently running on self-signed certificates. This will be resolved in the following steps.
All of the commands in this guide will need to be run as ‘root (sudo -s)’
For more information on other distributions the information can be found here: https://openvpn.net/vpn-software-packages/
Once installation is completed we need to create a password for the user ‘openvpn’ using the command:
We then need to login to the admin portal (https://your-server-ip:943/admin).
You will get an ‘not secure’ warning as the server is currently running on self-signed certificates. This will be resolved in the following steps.
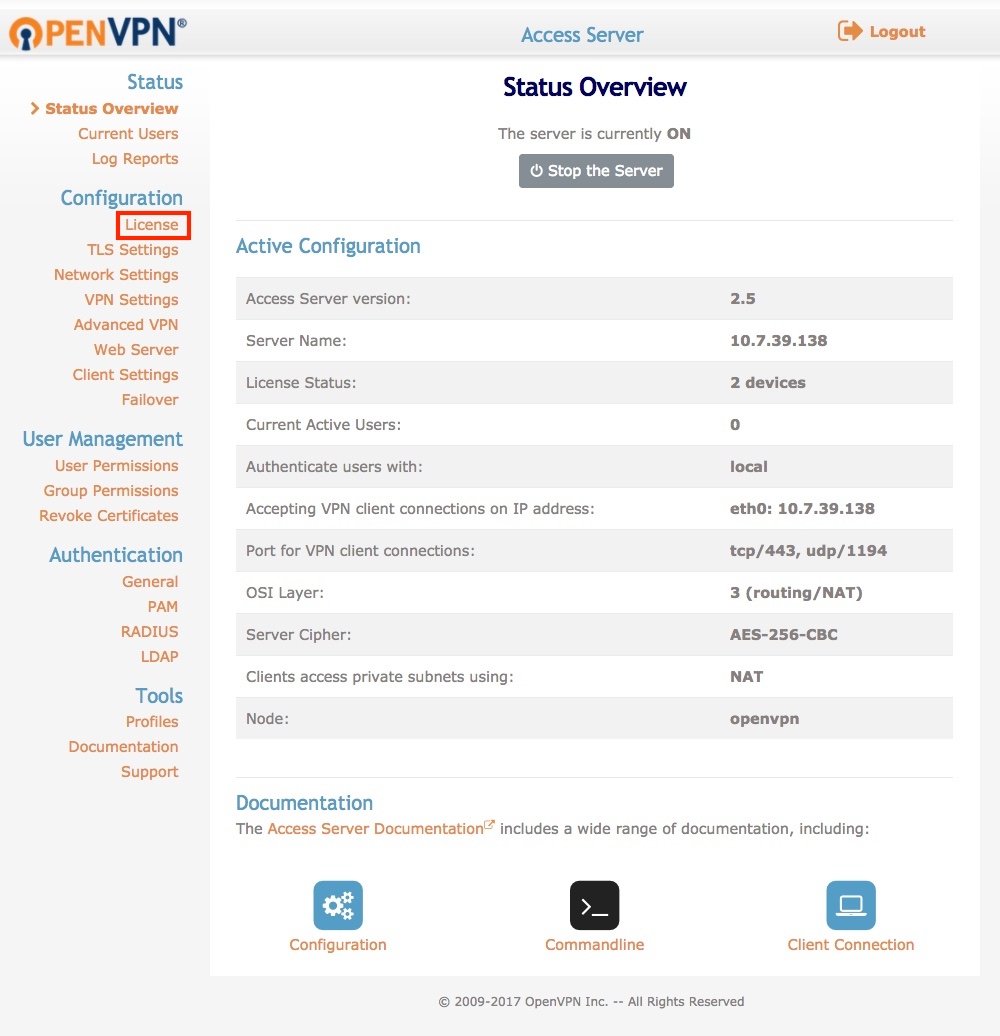
On the portal go to: Configuration > Network Settings and change hostname to your domain name (example.com) as shown in Figure 1.
Click save at the bottom and then ‘update running server’ (Figure 2)
To ensure you can access your Open VPN Server from outside you will need to forward the following ports on your firewall.
Certbot is an easy to use client that fetches a certificate from Let’s Encrypt and deploys it to a server. More information here (https://certbot.eff.org/)
To install Certbot on Ubuntu:
Once Certbot has been installed you can generate certificates for your domain using the following command:
The generated certificates will automatically be installed under /etc/letsencrypt/live/example.com as fullchain.pem & privkey.pem
If you have any errors common reasons include:
- Your DNS name is not currently pointing to your external IP. Check this with your domain provider.
- If you have a NAT/Firewall port 80 tcp may be blocked (check your firewall rules and/or router configuration).
- Make sure no other service is running on port 80 as Lets Encrypt uses it to for the http challenge. There are workarounds such as DNS challege or Nginx/Apache Plugins.
- Make sure you’re running commands as root
OpenVPN access server requires the certificates to be installed in it’s database, this can be done through the web interface or via the command line. As you have to renew Lets Encrypt certificates every three months we need to use the command line to ensure everything can be automated (step 3).
The following commands will install the certificates into the OpenVPN database:
#Install certificates & restart server
If everything is successful you should be able to browse example.com and have a secure login page with no certificate errors (Figure 3).
If you click on the lock & certificate you will be presented with the following window providing certificate information (Figure 4):
As mentioned previously in this guide, Lets Encrypt certificates expire every 3 months. To save us from having to renew & reinstall them manual we can create a simple bash script and schedule it using cron which is a time-based job scheduler.
- Copy the code below using a text editor of your choice into /usr/local/sbin/certrenewal.sh:
Openvpn Access Server Client Web Interface
2. Make the script Executable:
3. Enter Cron editor as root:
Openvpn Access Server Saml
This will schedule the script to run 'At 00:00 on day-of-month 1 in every 2nd month.'
(Crontab guru is great for determining expressions)
Install Openvpn Access Server Ubuntu
You can find me on the following: